Abstract
Current Mac OS X malware often persists and automatically starts by using the built-in launch system 1. This tool makes use of Automatic Folder Actions 2 in order to create a very basic but effective way of monitoring the addition of new launch objects to standard locations. In case a new object is placed in one of the monitored directories, a pop-up informs the user about the change, who then has in turn to decide if the change was legitimate or not. The new version is also monitoring locations where plug-ins are installed, for instance for common Internet browsers. The list of locations is displayed below. Besides displaying added files, this tool can also set up a log file where changes are recorded.
Mode of operation
The tools enables Automatic Folder Actions on the system and monitors the following locations (depending if the respective software is installed):
- /Library/LaunchAgents
- /Library/LaunchDaemons
- /System/Library/LaunchAgents
- /System/Library/LaunchDaemons
- ~/Library/LaunchAgent
- /Library/StartupItems
- /System/Library/StartupItems
- /Library/Internet Plug-Ins
- ~/Library/Safari/Extensions
- ~/Library/Application Support/Google/Chrome/Default/Extensions
- ~/Library/Application Support/Opera/widgets
- ~/Library/Internet Plug-Ins
- ~/Library/Containers/com.operasoftware.Opera/Data/Library/Internet Plug-Ins
- ~/Library/Containers/com.operasoftware.Opera/Data/Library/Application Support/Opera/widgets
If there is a file/folder added to any of theses locations, a notification script (which is included and copied to the User’s ‘Folder Actions Scripts’ folder) is executed which points to the change.
Screenshot
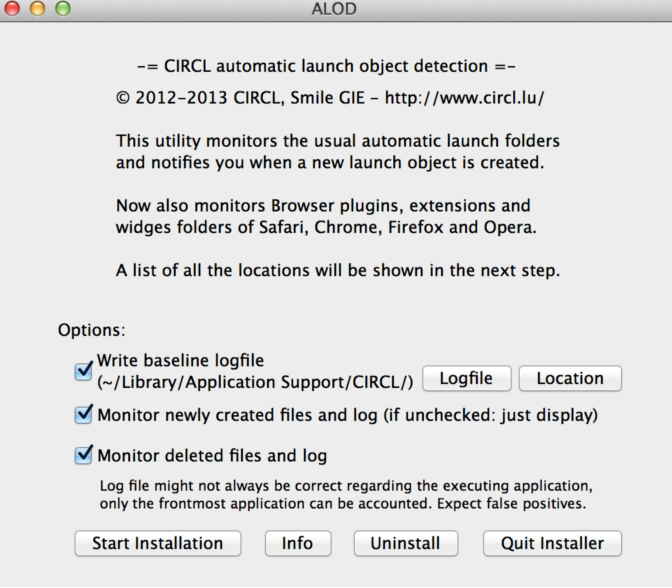
Installation
Download Installation package
Unzip this file and execute Install.app and follow the on-screen messages.
The current version of the .zip file has the following checksums:
- SHA1: afc8cb50c1e6bdb2b54932f47604c93cb19a717d
It contains two versions: a 64-bit version and a 32-bit version. For any recent machine, the 64-bit version should be used. If that doesn’t work, try the 32-bit version.
The previous version of the .zip file has the following checksums:
- MD5: 1ae11a5f9658af76314898d04666e341
- SHA1: 9b82161e97bf964a38b70c0d8f9424794b7374b6
The versions before had the following checksums:
- MD5: ef055f0432d204c4afd63a86298390bc
-
SHA1: e119a032e153033b3439b18c2f58037c90e54e1a
- MD5: c10a829185e85f1df90940eb071e6795
-
SHA1: b244c4330f95df1f4f1f5303970ba7593feef1d6
- SHA1: c23c653c7cd6788e56ae71c50aac57c77f3831e1
- MD5: ecdccfe167cb016cdc1dffbf630739b4
Deinstallation
Turn off Folder Actions and/or remove the monitoring for certain definitions in the same dialog. To get there, right-click any folder on your system and select Services - Folder Actions Setup
This installer includes a method to completely remove all Folder Actions and globally turn off Folder Actions.
History
- 2015-01-23: released new version avoiding a OS X Yosemite memory leak and other improvements
- 2013-04-09: released new version monitoring Internet plug-in folders.
- 2012-12-11: released rewritten version, properly signed with an Apple Developer ID
- 2012-11-23: released new version, now signed with an Apple Developer ID to address better Mountain Lion compatibility
- 2012-04-27: released new version
- 2012-04-26: removed wrong ~/Library/LaunchDaemons folder
- 2012-04-26: added new locations from deprecated SystemStarter 3
- 2012-04-20: initial version released
Credits
This work is based on an idea 4 by CNET’s Topher Kessler and contains many contributions from Chris Tomaziu (ctomnia at optusnet.com.au). Chris contributed code and was thoroughly testing buggy versions. Thanks Chris! Also thanks to the beta testers and their feedback, especially Marty Skinner.
Links
Legal disclaimer (Free Software License)
Copyright (c) 2012-2015, CIRCL, Smile GIE - http://www.circl.lu All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
- Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
- Neither the name of CIRCL nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
-
Quote from launchd(8) manpage: launchd manages processes, both for the system as a whole and for individual users. ↩
-
Quote from Automatic Folder Actions support page: Folder Actions let you automate common organizational tasks, such as moving items from one folder to another or moving an entire folder to a new location. ↩
-
SystemStarter(8) manpage: During boot SystemStarter is invoked by launchd(8) and is responsible for starting all startup items in an order that satisfies each item’s requirements. ↩
-
Monitor OS X LaunchAgents folders to help prevent malware attacks ↩

