What is Malware / Ransomware
Malware is any kind of malicious unwanted software which may prevent your PC from working properly. Ransomware is malicious software which deny access to your PC. The intruder likes to force you to pay some ransom to get back access again.
Goal of the paper
Depending on the Malware your computer is infected with, this paper could help you to get access back to your PC again.
Disclaimer
This Method, and if applicable any Related Instructions, are provided by the copyright holders “as is”. The goal of this Method and/or the Related Instructions, which were created based on a best effort basis, is meant solely for informational use. Any expressed or implied warranties, including, but not limited warranties of merchantability and fitness for a particular purpose are disclaimed by the Copyright holders. In no event shall the copyright holder be held liable for any direct, indirect or consequential damages arising in any way out of the use of this method and/or the related instructions. Method and/or related instructions ©CIRCL c/o SMILE g.i.e., 2012
Source of information
Executive summary
Depending on the kind of problem you have, one or the combination of some of the described methods could may help you to get access to your PC again.
If your system do not boot anymore in a good way, you can try to boot in “Safe Mode”.
Once you have access to at least a command line interface, you can try to remove malicious “Windows Registry” entries, troubleshooting the boot process, inspect the “Task Scheduler” and/or perform a System Restore.
MS Windows provides multiple locations where a malicious program could be launched automatically during system boot or user login. Here you find instructions, how to check for the most common used locations.
All this information came from websites owned by Microsoft. We found many texts which describe the methods for Windows XP and other outdated Windows versions. Therefore this paper mainly address Windows 7.
CIRCL always recommends to reinstall a compromised system because there might remain some artefacts leading to a reinfections.
Boot in “Safe Mode”
If your PC does not boot proper anymore, you should try to boot the system in the restricted “Safe Mode”.
Within “Safe Mode” Windows loads only a minimalistic set of drivers and programs at startup. The chance is high that this will provide you a running system what you can use to analyze and fix the system.
Power up your system and immediately start pressing F8 key several times until you get the “Advanced Boot Options” window. There you should select “Safe Mode with Command Prompt”.
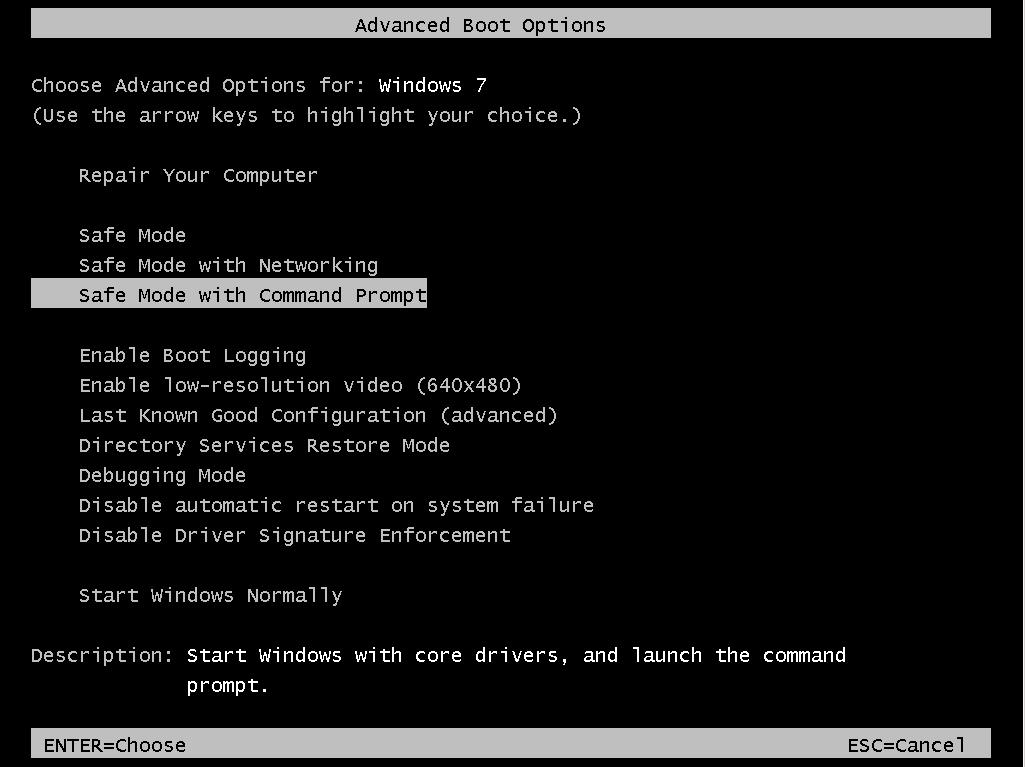
The Operating System will now boot in “Safe Mode”. You should log in with an administrative account and get an command prompt environment.
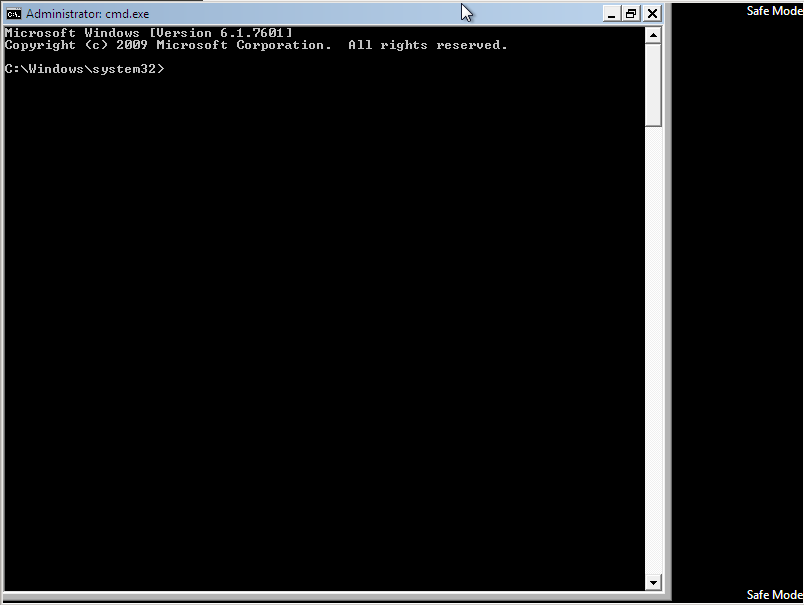
Within the command prompt environment in “Safe Mode”, you can enter commands like “msconfig”, “regedit”, “C:\Windows\explorer” or “explorer”.
Startup-folder
Programs in the Windows startup-folder run automatically when a user logs in. There is an “all users” startup-folder which works for all the users. There are also user specific startup-folder for each single user.
The hidden startup folder for the current user is located at: “C:\Users<user-name>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”
To easily open the current users startup-folder:
-
Open the Windows “Start Menu” and click “All Programs”
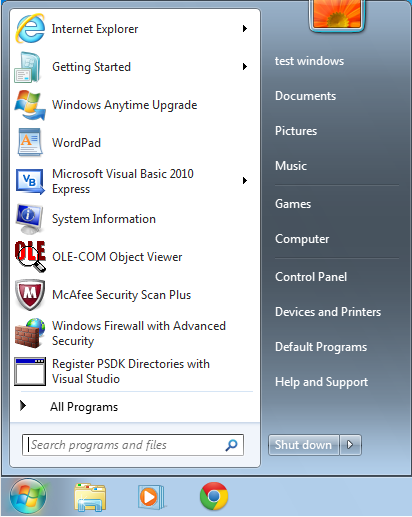
-
Right click the “Startup”-folder and select either the “Open” or the “Explore” option.
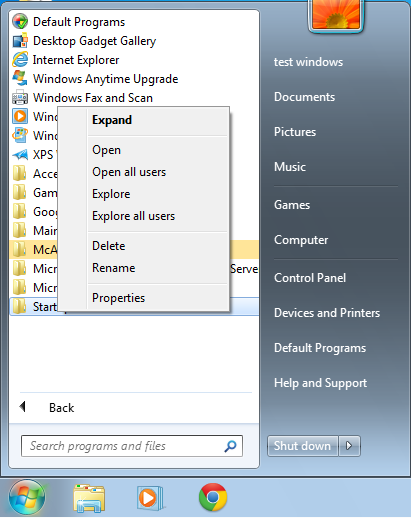
The hidden all users startup folder is located at: “C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup”
To easily open the all users startup-folder:
-
Open the Windows “Start Menu” and click “All Programs”

-
Right click the “Startup”-folder and select either the “Open all users” or the “Explore all users” option.

Windows Registry Key
There are several places within the Windows Registry where startup programs could be configured. We will inform you about the most common places abused by malware. We show you how to manually search the Registry for malicious entries. Be aware that we take nor responsibilities for the case you damage your system (see 3. Disclaimer).
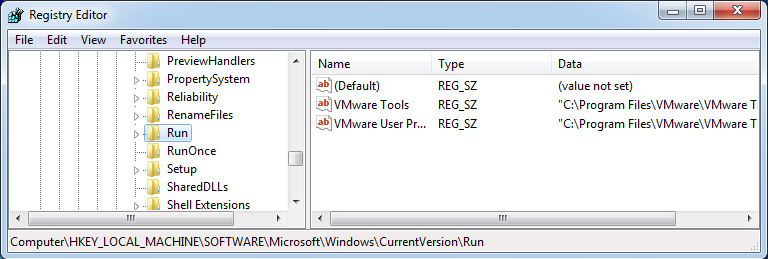
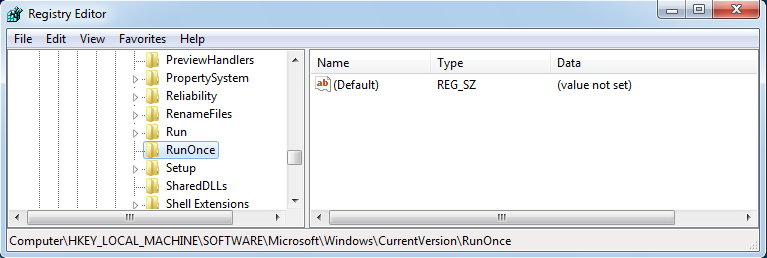
In most cases you find two kinds of locations for startup programs in the Windows Registry. Programs at locations ending with “Run” run every time when Windows start. Programs at locations ending with “RunOnce” run only once at the next time that Windows start.
To launch the tool for manually editing the Windows Registry, enter “regedit” at the Windows “Start” menu.
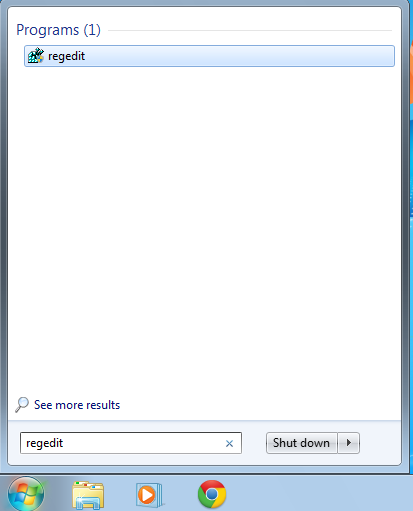
The “User Account Control” UAC may ask you for permission to launch this program because it can do major changes on the PC. If the verified publisher is “Microsoft Windows” you can accept by selecting “Yes”.
To review the settings for the current user navigate to the two locations:
- “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”
- “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce”
To review the settings for All users navigate to the two locations:
- “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run”
- “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce”
If your Windows is managed by a group policy, there are some additional locations to check for startup-programs:
- “HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run”
- “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run”
For 64-bit systems there are two additional locations you have to check:
- “HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run”
- “HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\RunOnce”
Additional places within the Windows Registry:
- “HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows”
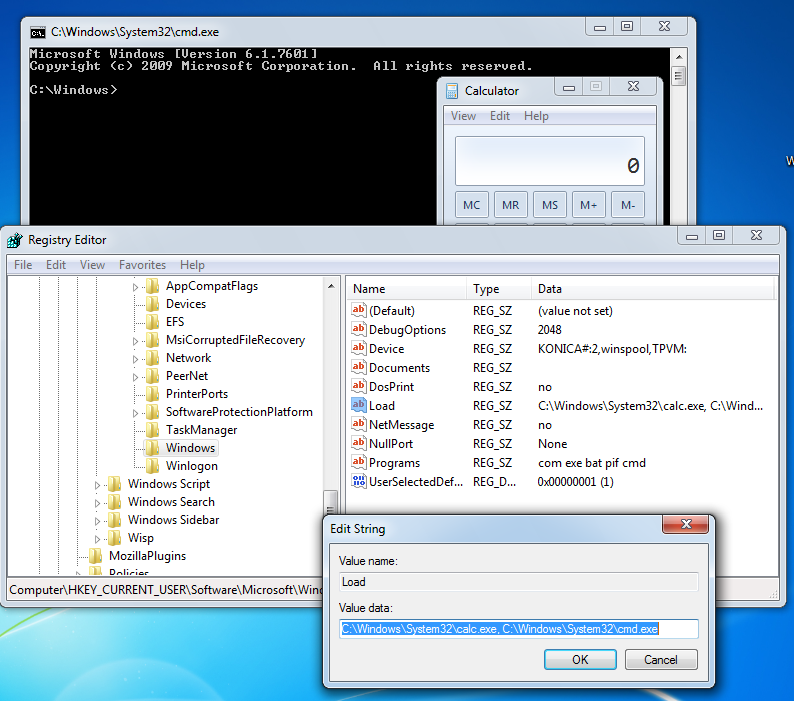
Every program in the “Load” value of the Windows registry key will be executed, when a user log in
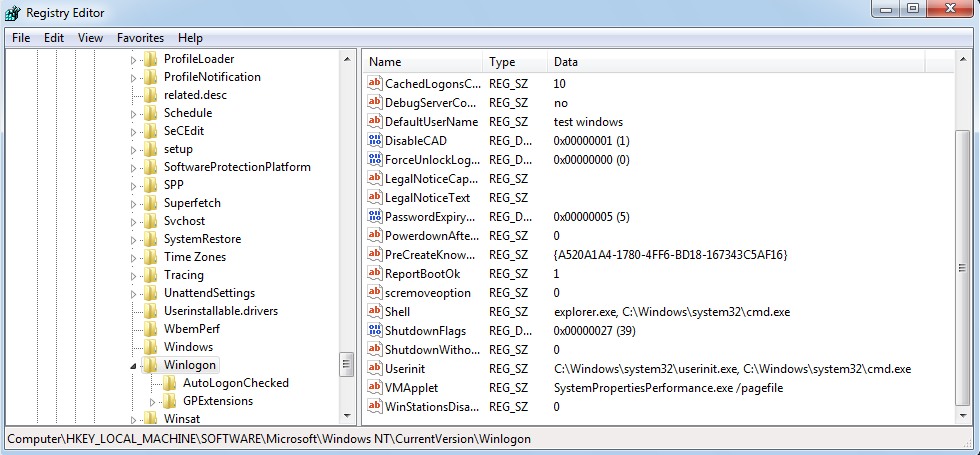
- “HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon”
- Im Winlogon Registry key the default value of “Shell” is: “explorer.exe”
- The default value of “Userinit” is: “C:\Windows\system32\userinit.exe”
In this example we add for both Values “, C:\Windows\system32\cmd.exe” to launch the “cmd.exe” program two times, when a user logs in.
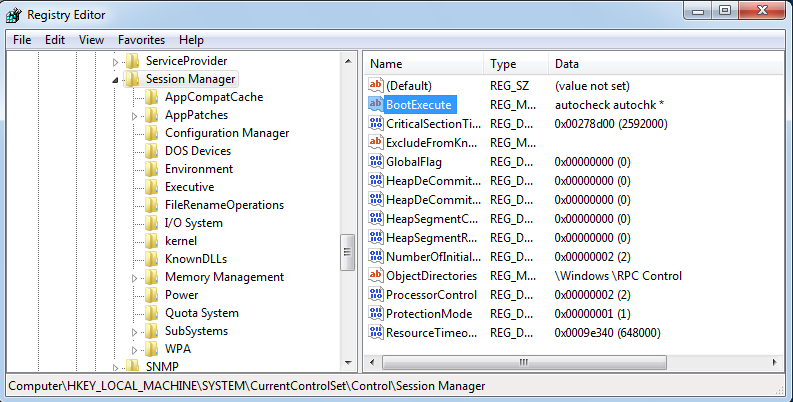
- “HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Session Manager”
The value of “BootExecute” id set by default to “autocheck autochk *”. This causes Windows to check the file-system during startup. You have to ensure that this value is not changed.
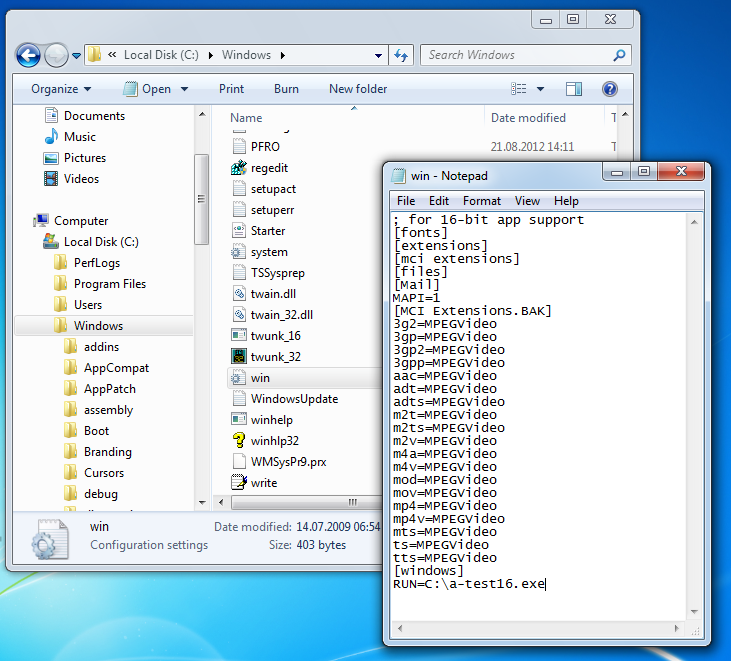
The file C:\Windows\win.ini is a legacy configuration file left back from Windows 3.11. It still could be used to load 16-bit programs. Review the content of this file and search for “LOAD=” or “RUN=” lines.
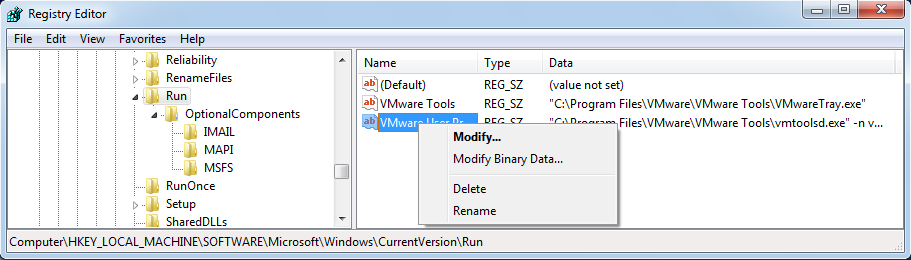
If you discover a suspect Registry Key which you like to remove, right click the suspect startup program and SELECT “Delete”.
Task Scheduler
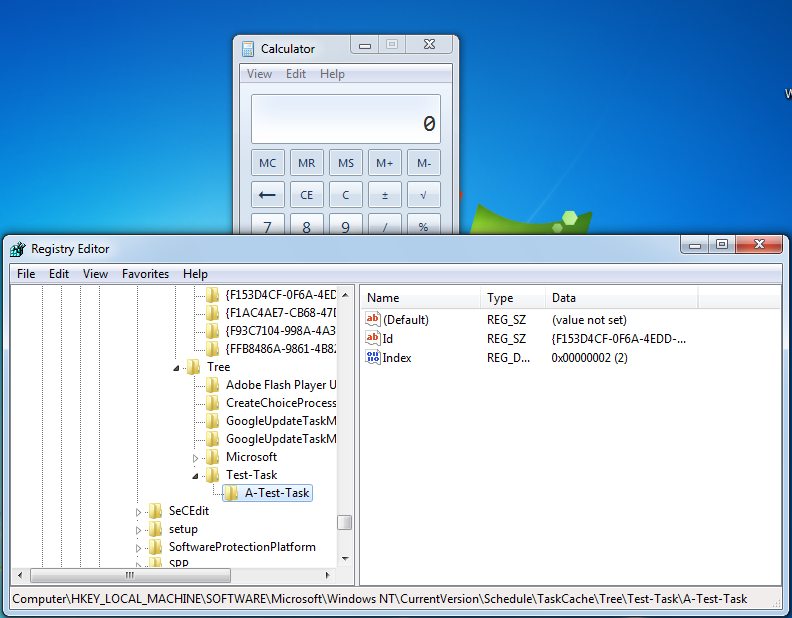
An other way to automatically launch programs under Windows is the “Task Scheduler”. A first impression to see which applications are launched is to review the Windows Registry: “HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\”
In this example we like to disable the task “A-Test-Task” which automatically launches the Calculator after a user login.
Open the “Task Scheduler” by entering “taskschd.msc” in the Windows “Start” menu:
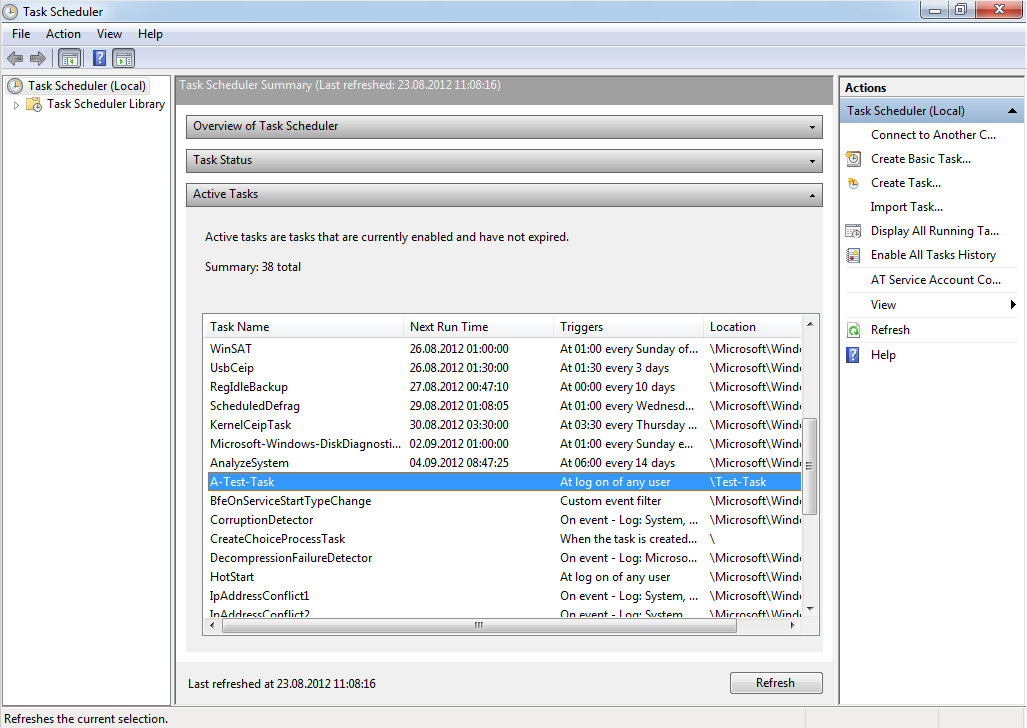
In the middle pane of the Task Scheduler you have the “Active Tasks” section. The “Triggers” column gives information about the event which was triggers the task.
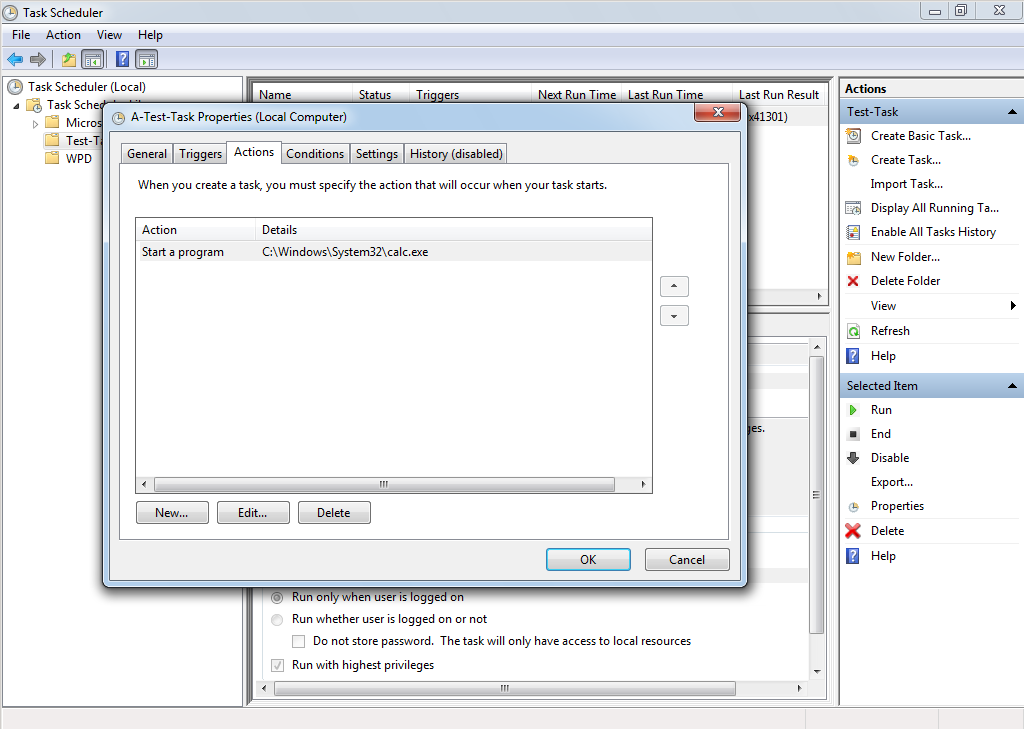
By double clicking at the suspect task, we get information about the actions, conditions, settings and other details about it.
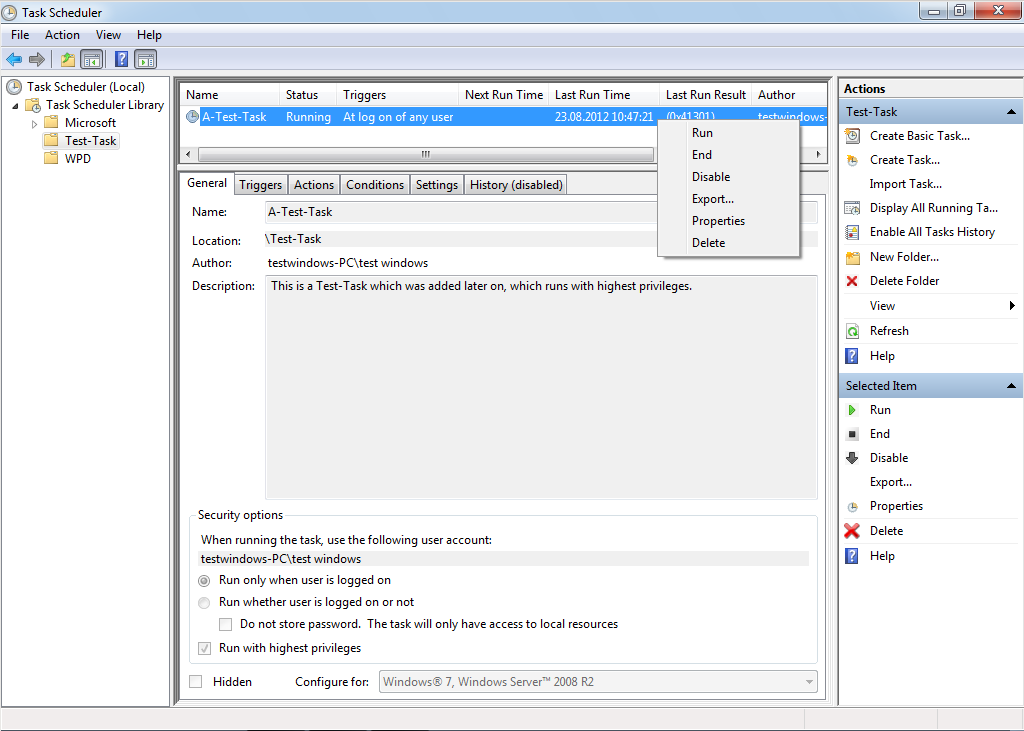
It is possible to “Disable” the task and check if the system issues are resolved at the next reboot.
System Restore
Windows 7 automatically sets a restore point, each time before a program/service is installed/installed and before a windows update is installed. You also could use the System Configuration utility to manual set restore points.
If your system runs into trouble, you can use the “System Restore” functionality to set back the configuration to an older restore point of a date when the system works properly.
Enter the command “msconfig.exe” either at the Windows Menu or within the command prompt (if you run in Safe Mode).
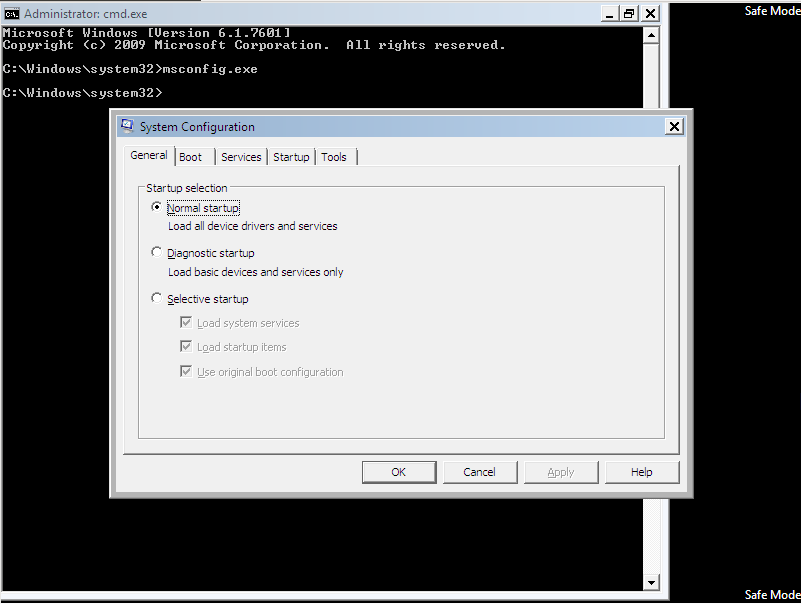
In the System Configuration utility under the “Tools”-Tab select “System Restore” and push the “Launch”-Button to launch the System Restore utility.
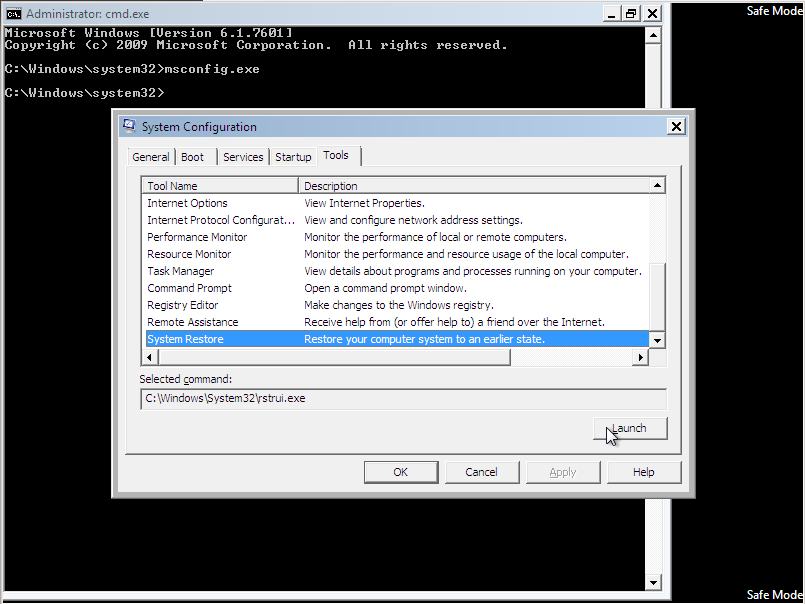
If you know how the System Restore work, press the “Next”-Button. Otherwise get some support from the provided link.
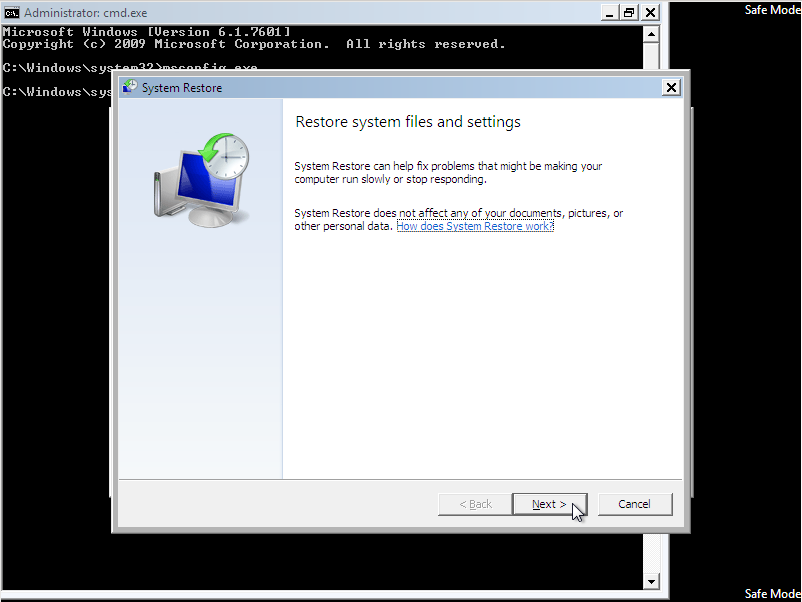
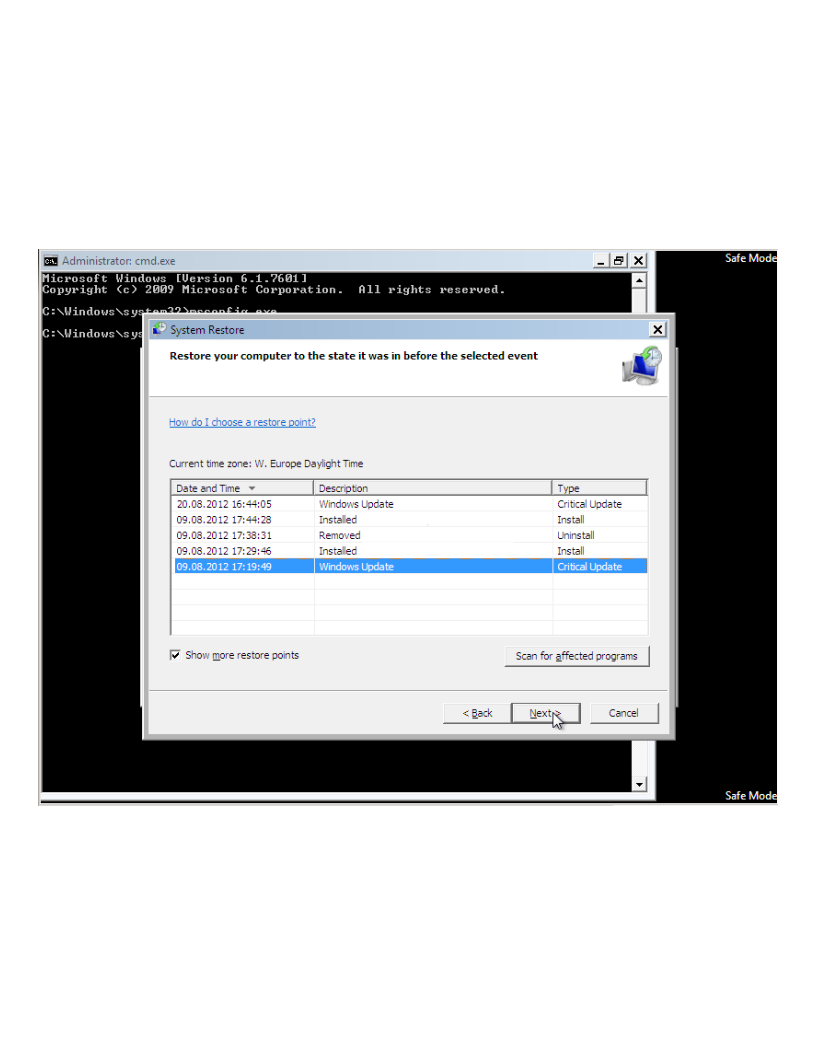
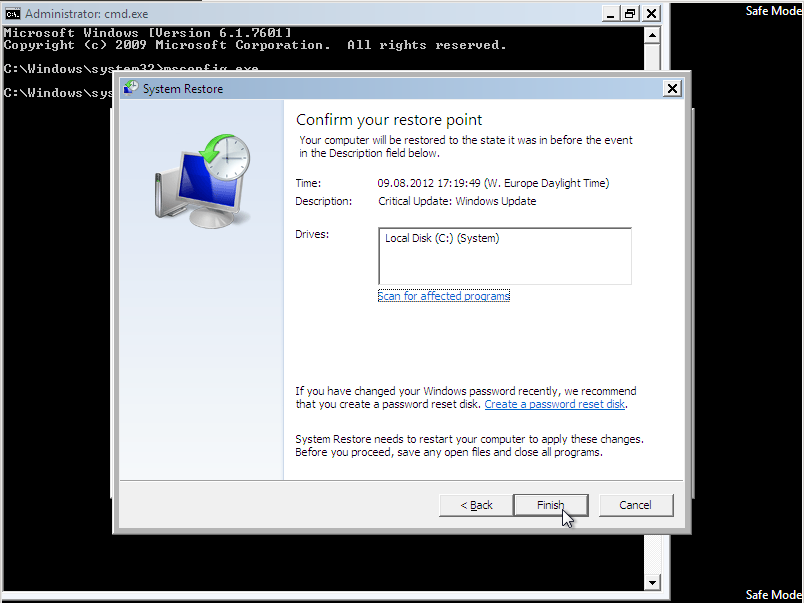
Activate the “Show more restore points” check-box to see more possibilities. Select the Restore Point you like to go back to and click the “Next” Button. The “Scan for affected programs” Option provides you with additional information about what programs will be affected.
At the “Confirm your restore point” stage of your activity ensure to read all the details before starting the action by clicking the “Finish”-Button.
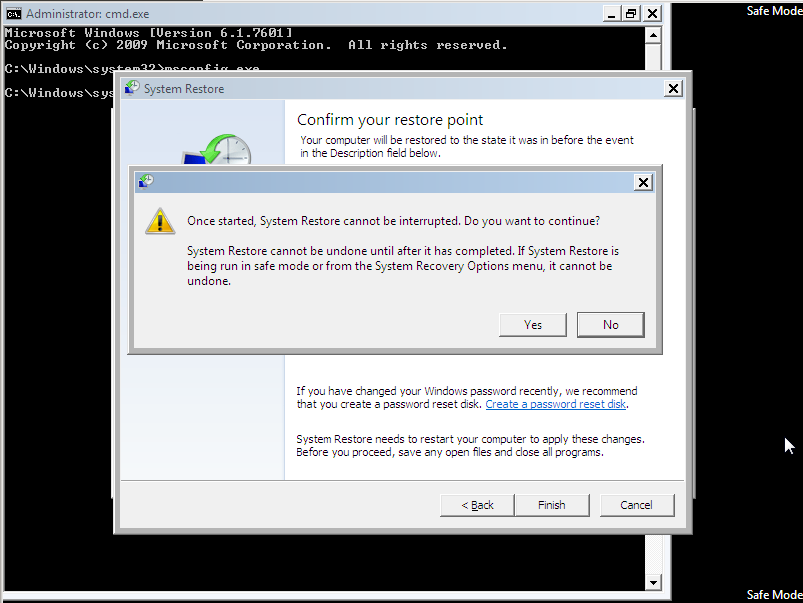
Once System Restore is started it cannot be interrupted and undone until it has completed.
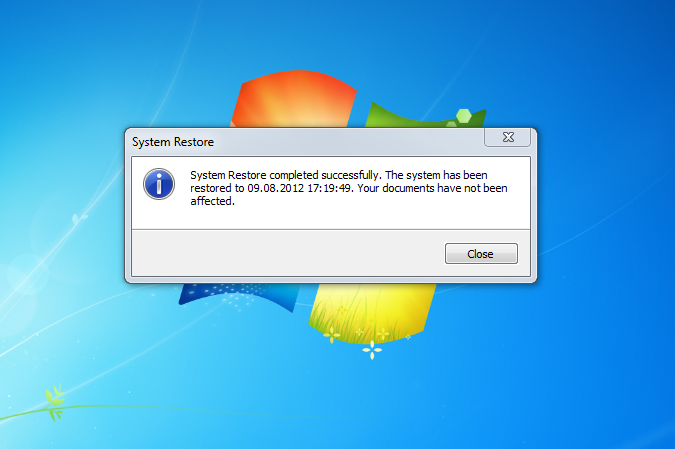
After clicking “Yes” the System Restore will start and will end with a System Reboot.
Diagnostic Startup
If your system does not properly boot, you can use the msconfig.exe tool to debug the boot process.
Enter the command “msconfig.exe” either at the Windows Menu or within the command prompt (if you run in Safe Mode).

In the System Configuration utility under the “General”-Tab select “Diagnostic startup” and push the “OK”-Button.
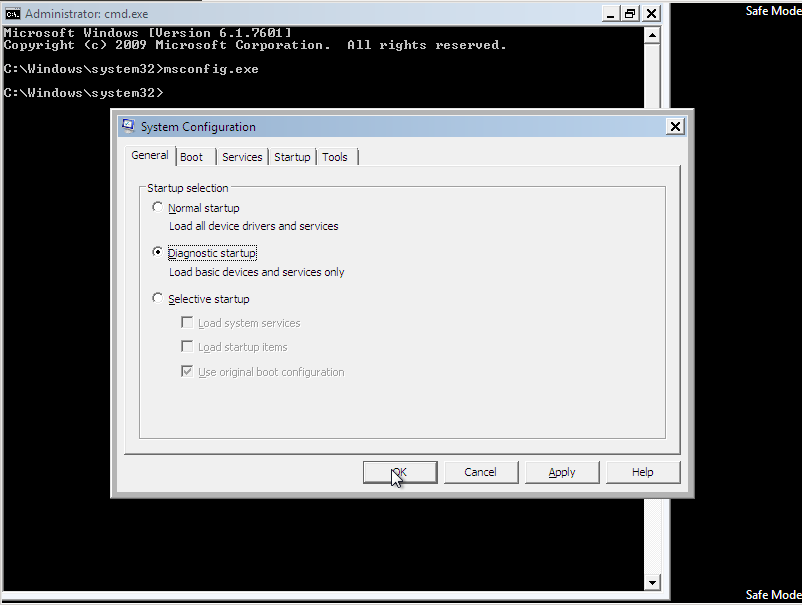
You need to start your system
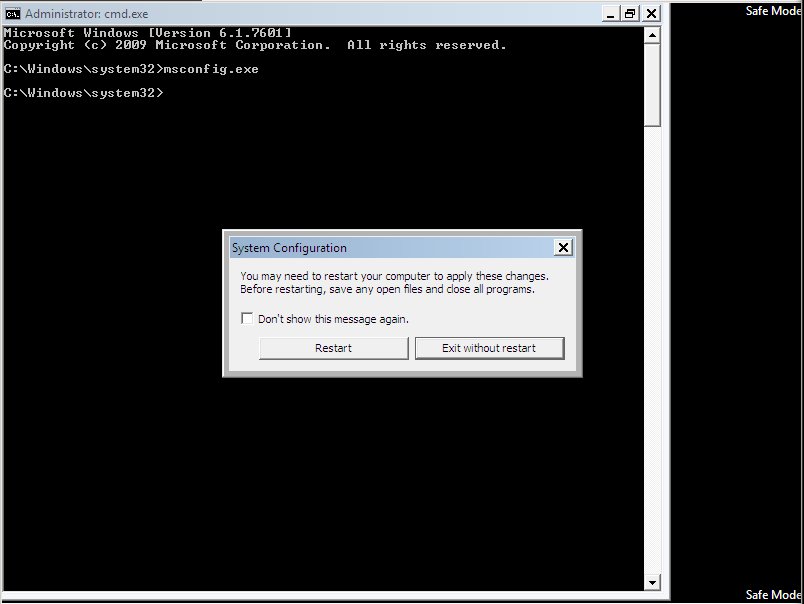
Your system will restart with only basic devices and services only. If the problem now do not occurs anymore, try to find the problem by turning individual startup program’s and services on or off.
Selective startup
Selective startup let you choose, which programs and services should load during system startup. The goal is to identify the program or service which causes the problems.
Launch the System configuration utility by entering “msconfig.exe” like described under “11. Diagnostic Startup”
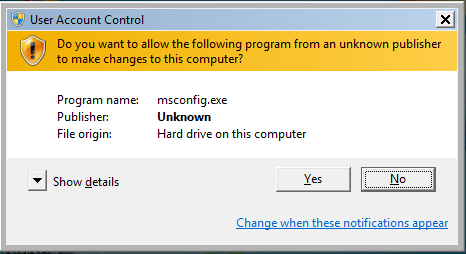
Since only limited services are running, the User Account Control could not validate the publisher of the software. You have to click “Yes”, to continue.
In the “General”-Tab of the System Configuration utility now the option “Selective startup” is selected by default.
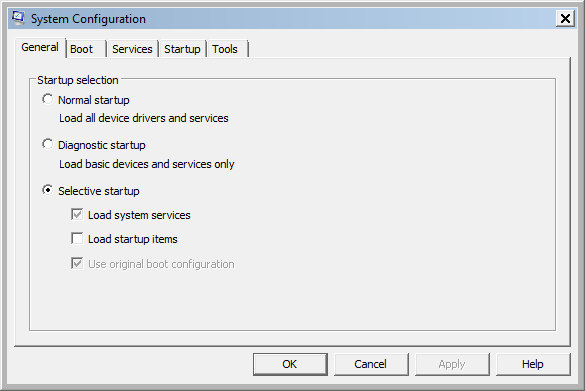
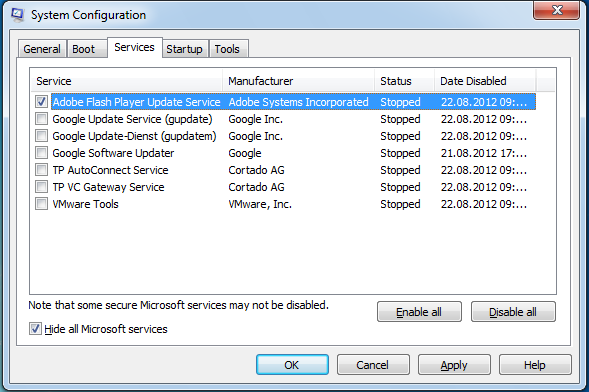
Under the “Service”-Tab most of the services are disabled at this point. Just a view services are enabled.
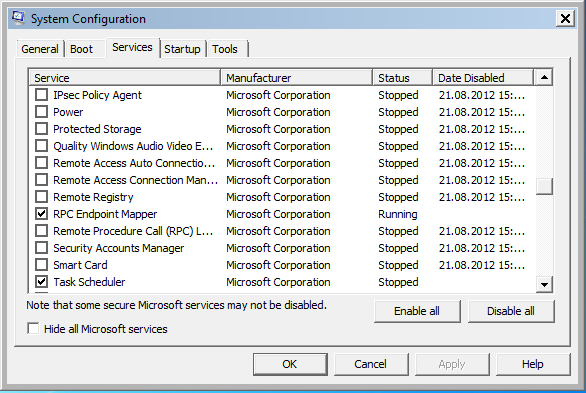
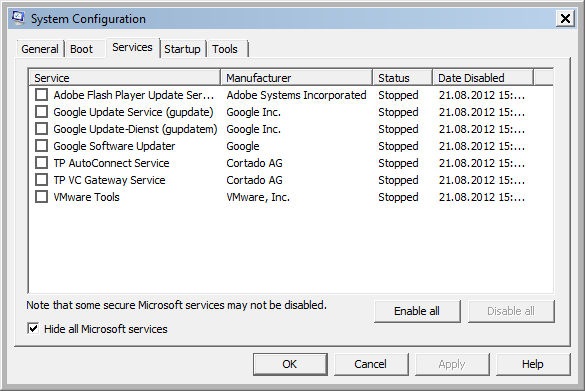
At this point the “Hide all Microsoft services” check-box is very useful. Activating this option hide all valid Microsoft services. Very often a non MS service is responsible for the problems.
Under the “Startup”-Tab you can select what programs to start during system boot.
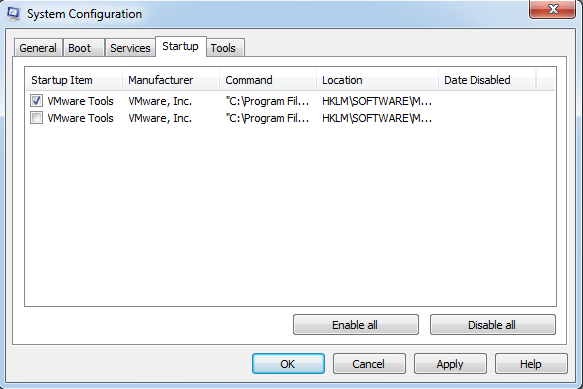
You can individually activate one single service step by step to identify the source of the problem. You could reach a fast result by following this best practice instructions:
-
Push “Enable all”-Button to activate all services
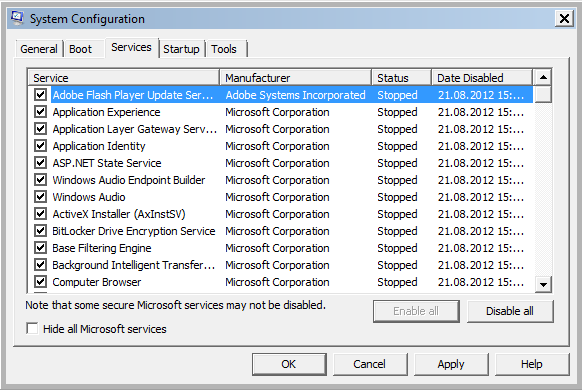
-
Activate “Hide all Microsoft services”
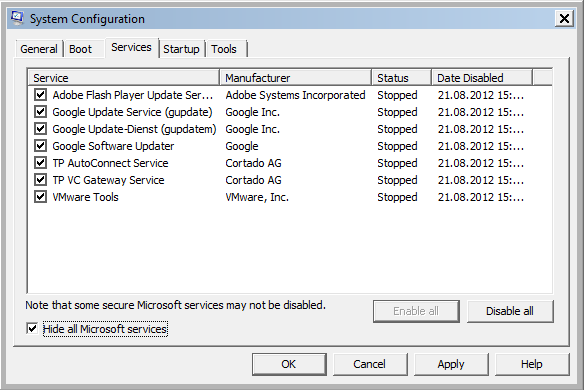
-
Push “Disable all”-Button to deactivate all the No Microsoft services
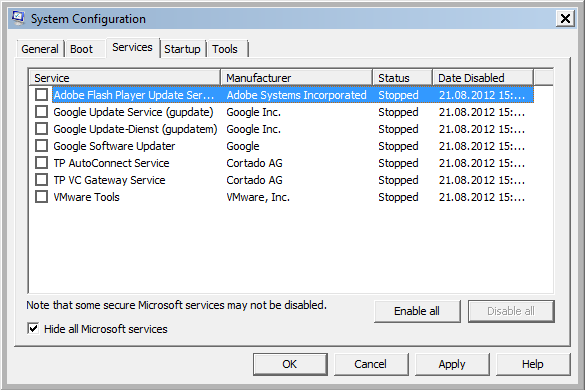
-
Deactivate “Hide all Microsoft services”. This is necessary because otherwise the changes on the Microsoft services did not apply. This could be a bug or a feature of the msconfig.exe tool.
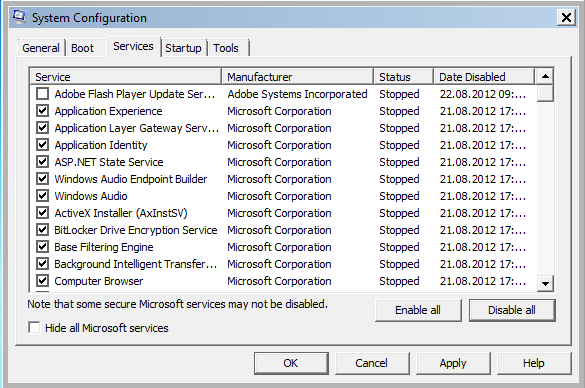
Press the “Apply”-Button and than the “OK”-Button. In the upcoming Dialog press “Restart” too reboot the system.
If the system reboots in a good manner, activate each no Microsoft service, step by step, in combination with a reboot. Like that you could quickly identify the source of the problem.
Do the same with the “Startup” programs.

